1. Information security risk management structure
The Company's Information Technology Department is an independent department that is not affiliated with the user unit. The head of the Information Technology Department serves as the information security manager, and the RS Resource Service Group serves as the information security processing team.
The Information Technology Department is responsible for coordinating and implementing information security policies, promoting information security messages, enhancing employee security awareness, and collecting and improving technologies, products or procedures for the performance and effectiveness of the organization's information security management system.
Develop a crisis notification operation method for information security incidents, detailing the action steps when an information security incident occurs, including incident detection, response, recovery and follow-up analysis. Regular drills and updates ensure effective operation in a real crisis situation.
The information audit team conducts information security audits on the internal control system-computer cycle every year to evaluate the effectiveness of the company's internal controls on information operations.
The Document Control Team ensures that information security policies, procedures and standards are effectively implemented, continuously updated, and understood and adhered to by all relevant personnel within the organization. Ensure all security-related documents go through appropriate review and approval processes and are version controlled.
Report the operation status of information security risk management to the board of directors at least once a year. The company was report on March 2024.
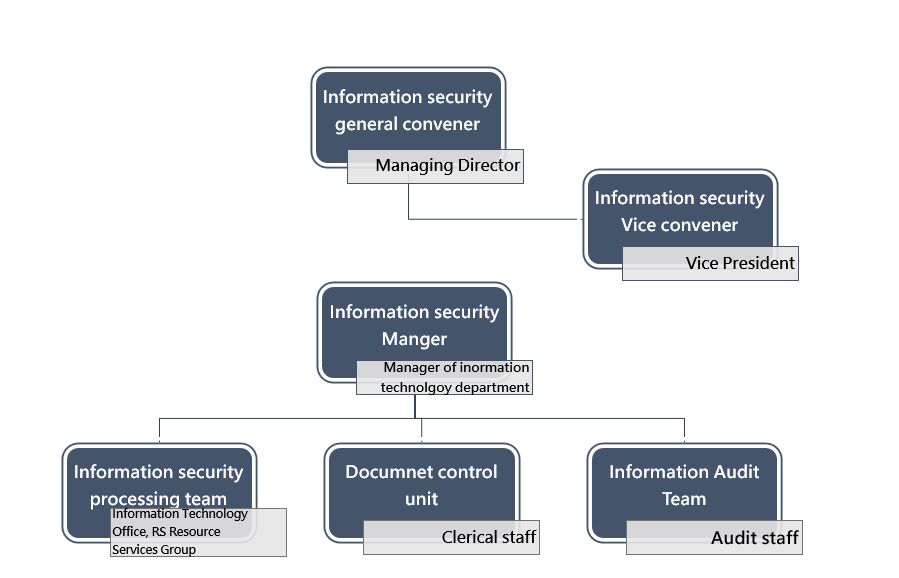
2. Information security policy and specific management plan
(1) Internet information security control
♦Erect a firewall (Firewall)
♦ Regularly scan computer systems and data storage media for viruses
♦The use of various online services should be carried out in accordance with the information security policy
♦Regularly review the System Log of various network services and track abnormal situations
(2) Data access control
♦Computer equipment should be taken care of by dedicated personnel, and account numbers and passwords should be set
♦Grant different access rights based on functions
♦The transferred personnel will have their original permissions revoked
♦Confidential, sensitive information and copyrighted software should be removed or overwritten before equipment is scrapped
♦Remote login to the management information system should be subject to appropriate approval
(3) Strain recovery mechanism
♦Regularly review emergency response plans
♦Regular system recovery drills every year
♦Establish a system backup mechanism and implement off-site backup
♦Regularly review computer network security control measures
(4) Propaganda and inspection
♦Promote information security information at any time to enhance employee security awareness
♦Perform regular information security inspections every year and report to the responsible supervisor
(5) In order to implement information security management, the company has established an internal control system - computer circulation and information management measures. Through the joint efforts of all colleagues, we hope to achieve the following policy goals:
♦Ensure the confidentiality, integrity and availability of information assets.
♦Ensure data access is regulated according to department functions.
♦Ensure the continuous operation of information systems.
♦Prevent unauthorized modification or use of data and systems.
♦Perform information security audits regularly to ensure information security is implemented.
(6) Join TWCERT/CC Taiwan Computer Network Crisis Management and Coordination Center
♦ Obtain real-time security threat information and strengthen corporate information security.
♦ Obtain professional technical support and consultation, and share information with other members.
♦Regularly participate in cybersecurity-related training and education activities organized by the center.
3. Information security education, training and maintenance
The company's security resources and maintenance included the replacement of anti-virus software versions, the replacement of group information equipment, the renewal of group dedicated lines and corporate information security protection and various maintenance contracts. In 2023, total investment expenses were NT 4,748 thousand dollars.
The company conducts information security education and training for employees every year. In 2024, the total number of people attending classes was 34 people, and the class hours were 136 hours. The company invited external information security lecturers to the factory to explain external hacker intrusion fraud techniques and prevention awareness. The company also promote the latest information security concepts to all employees to reduce risks, hoping to enhance the information security awareness of all employees, and through the external email filtering mechanism , company computers deploy security protection software, network firewall mechanisms and company computers deploy anti-virus software to protect the company's rights and interests anytime and anywhere.